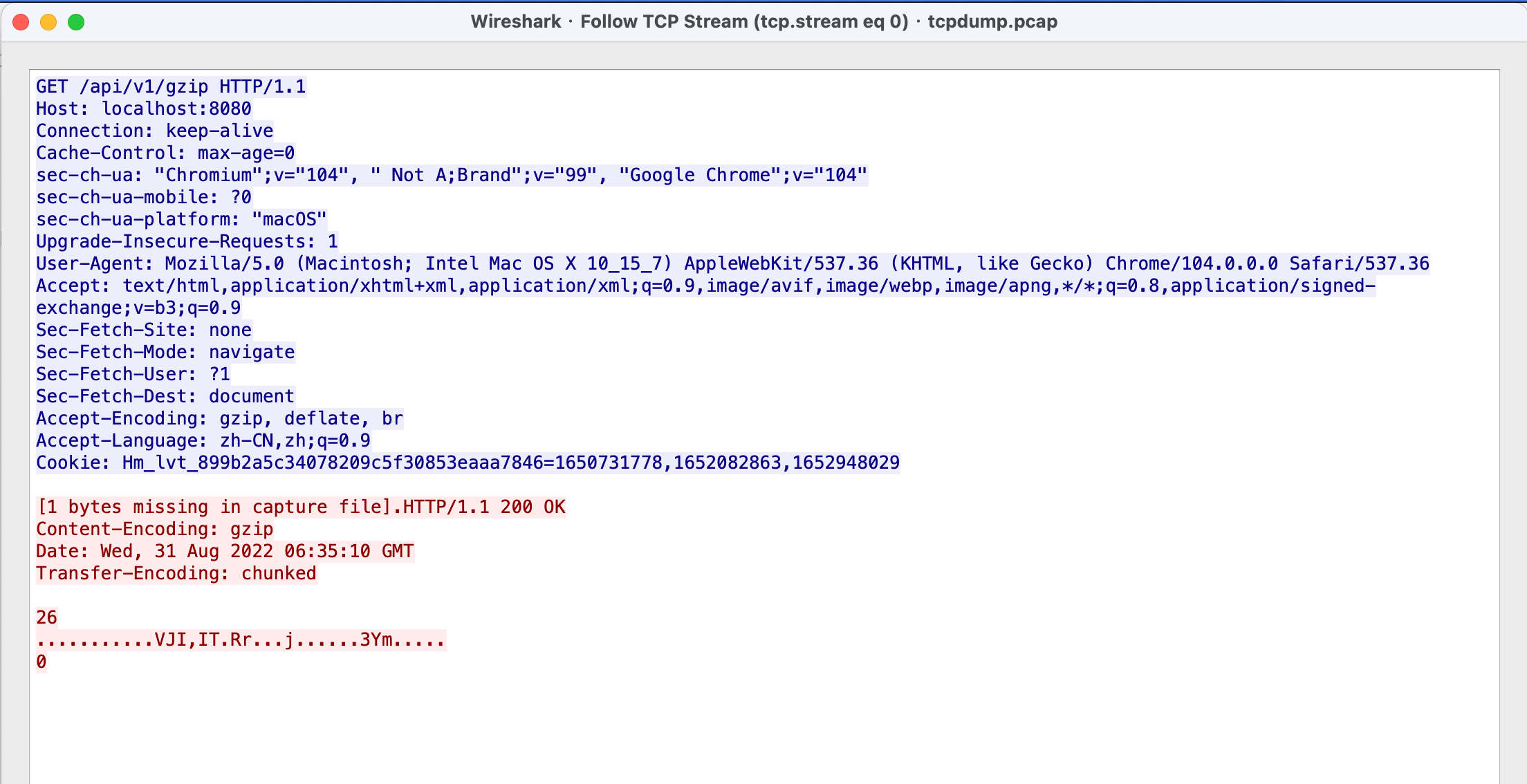
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
| fanhaodong.516:go-sdk/ $ sudo tcpdump -i eth0 'port 8888' -l -n -X | bin/gtool tcpdump [14:08:10]
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on eth0, link-type EN10MB (Ethernet), capture size 262144 bytes
14:08:51.426622 IP 10.225.xx.196.28284 > 10.248.xx.215.8888: Flags [S], seq 174152772, win 28200, options [mss 1410,sackOK,TS val 445695352 ecr 0,nop,wscale 10], length 0
14:08:51.426726 IP 10.248.xx.215.8888 > 10.225.xx.196.28284: Flags [S.], seq 2533803252, ack 174152773, win 28960, options [mss 1460,sackOK,TS val 2106570914 ecr 445695352,nop,wscale 10], length 0
14:08:51.430699 IP 10.225.xx.196.28284 > 10.248.xxx.215.8888: Flags [.], ack 1, win 28, options [nop,nop,TS val 445695357 ecr 2106570914], length 0
14:08:51.430790 IP 10.225.xx.196.28284 > 10.248.xxx.215.8888: Flags [P.], seq 1:987, ack 1, win 28, options [nop,nop,TS val 445695357 ecr 2106570914], length 986
{
"method": "SimpleTestRPC",
"seq_id": 324,
"protocol": "UnframedBinary",
"message_type": "call",
"payload": {
"1_STRUCT": {
"255_STRUCT": {
"1_STRING": "111",
"2_STRING": "xxxx.xxx.xx",
"3_STRING": "10.xxx.xxx.xxx",
"4_STRING": "",
"6_MAP": {
"cluster": "test",
"env": "prod",
"idc": "xxx",
"tracestate": "_sr=1",
"user_extra": ""
}
},
"1_STRING": "hello world"
}
},
"meta_info": {}
}
14:08:51.430803 IP 10.248.xxx.215.8888 > 10.225.xxx.196.28284: Flags [.], ack 987, win 32, options [nop,nop,TS val 2106570918 ecr 445695357], length 0
14:08:51.432384 IP 10.248.xxx.215.8888 > 10.225.xxx.196.28284: Flags [P.], seq 1:890, ack 987, win 32, options [nop,nop,TS val 2106570919 ecr 445695357], length 889
{
"method": "SimpleTestRPC",
"seq_id": 324,
"protocol": "UnframedBinary",
"message_type": "reply",
"payload": {
"0_STRUCT": {
"1_STRING": "hello world",
"2_STRING": "hello, world!",
"255_STRUCT": {
"2_I32": 0,
"1_STRING": "",
"3_MAP": {
"_CUSTOM_CLUSTER": "default",
"_CUSTOM_ENV": "prod",
"_CUSTOM_IDC": "xxx",
"_CUSTOM_IP": "10.xxx.xx.xx",
"_CUSTOM_IP_V4": "xxx.xxx.xxx.xxx",
"_CUSTOM_IP_V6": "xxxx",
}
}
}
},
"meta_info": {}
}
14:08:51.436438 IP 10.225.xx.196.28284 > 10.248.xxx.215.8888: Flags [.], ack 890, win 31, options [nop,nop,TS val 445695362 ecr 2106570919], length 0
14:08:51.637336 IP 10.225.xx.196.28284 > 10.248.xx.215.8888: Flags [F.], seq 987, ack 890, win 31, options [nop,nop,TS val 445695563 ecr 2106570919], length 0
14:08:51.637552 IP 10.248.xx.215.8888 > 10.225.xx.196.28284: Flags [F.], seq 890, ack 988, win 32, options [nop,nop,TS val 2106571125 ecr 445695563], length 0
14:08:51.641670 IP 10.225.xx.196.28284 > 10.248.xxx.215.8888: Flags [.], ack 891, win 31, options [nop,nop,TS val 445695568 ecr 2106571125], length 0
|
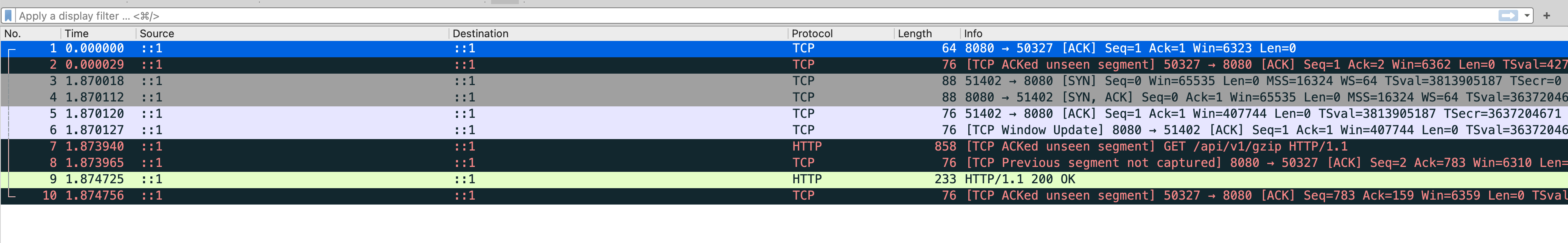 5. 使用 flow 可以更好的查看连接上的请求!
5. 使用 flow 可以更好的查看连接上的请求!